As the ICT space grapples with the concept of “Zero Trust” and tries to formulate what it means in a standard way, vendors are rushing to release products on their own definitions of what “Zero Trust” should mean. Here are my fast thoughts.
-
- It mustn’t become another way of creating fences and moats. It’s more than a new way of doing access control policies.
- It needs to factor into play a new world of interworking at speed and scale.
- Security is not a technology, not just about securing assets, it’s more. It must also mean covering business assurance.
- The extent of architecting “Zero Trust” should essentially mean resetting security every time and factoring a new dimension – context.
- The context will be king in Security, and thus the need to incorporate the concept of Security Intelligence, as part of a larger set of Intelligence Management functions.
- Security and Privacy are different concepts albeit sharing the same underlying principles of confidentiality, integrity, and trust.
- Security and Privacy must both be considered separately and together when reviewing what it means to context.
- Shift from reactive Security measures to real-time context-aware and context-bound security activity
- Bring users into the decision matrix of guard railing security operations and administration.
- Trust boundaries are an old way of identifying security concerns. While security perimeter is important to understand how to implement controls and policies, this is no more an enabling business practice. Security concerns stretch beyond any perimeter and must be considered as a fluid state of a continuously changing environment.
- Data is the usual target for security breaches, but the conduit is the process in place. Processes need that context-aware, context-bound capability to effectively support the dynamic state of managing, and administering security.
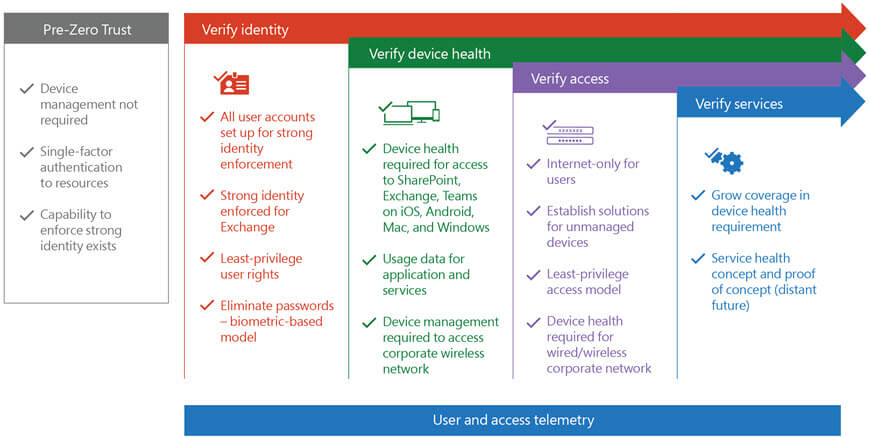
Microsoft’s view of the major components of Zero Trust by phases.
In a recent publication Security Boulevard, Rich Smith hints that “Being able to continuously authenticate users’ access to critical web and API services without causing them to pay the price of increased friction may sound like a lofty goal, but it can be achieved through the integration of technologies you likely already have. By combining technologies built to continuously monitor applications and APIs for attacks and anomalous behavior with identity technologies already deployed to authenticate users give administrators the ability to protect their critical applications without unduly inconveniencing the user.”
While this is basic and true, I think if the focus for ZT is put squarely on authentication, and thus building multi-factor authentication systems then the rise in social engineering and spoofing will make implementing and handling new innovative processes a challenge, while diminishing the experience users. I’ve been pretty upset seeing how authentication is implemented on certain sites, the approach to Zero Trust on these platforms seems to lack some common sense about being context-aware and context-bound. It puts a burden on proof on the user, understandingly so, but when I’ve used one device to access the same site several times, some context-awareness has been established, and additional patterns have been availed based on my data-print. One will think this information will be integrated into the implementation of ZT in a way as to equally make security management a delightful experience.
Ask any CISO about a trend that they think will help push security postures forward and you’ll inevitably hear the same thing: the elimination of the perimeter and the rise of the zero trust mindset. In the old perimeter model, users were typically only authenticated once to access the network, while with many zero trust approaches users are much more frequently authenticated. However, this creates a clear challenge of “usability vs. security” that every CISO is all too aware of: using short enough session.
Also, the concept of authentication shouldn’t be one that needs to always be escalated to the end-user for input. Authentication should happen at the device, connection, and application levels that enable the concept of continuous authentication, and yet even more than that to enable new forms of managing the connection security, user data security, application security, and interface security.
Read more about other ideas around Zero Trust here: The Future of Zero Trust: Continuous Authentication – Security Boulevard